Article
Securing a kiosk from the software side
Building a secure kiosk means more than just choosing the right enclosure - there are many considerations that have to go into software configuration to prevent someone from crashing the system Â… or worse.
March 31, 2005 by James Bickers — Editor, Networld Alliance
Building a secure kiosk means more than just choosing the right enclosure - there are many considerations that have to go into software configuration to prevent someone from crashing the system Â… or worse.
Indeed, when most people think about the security of a kiosk, their first thoughts turn to physical security: How durable is the enclosure? Can the keyboard be easily removed and stolen? Is the monitor easily breakable?
But equally important is the application that kiosk is running, and how well it keeps users from accessing features of the machine that they are not supposed to. A nice, shiny new kiosk will quickly become an expensive headache if users can, for instance, access the Windows control panel, modify the registry or gain the ability to browse directories and delete files.
Donald Mothersbaugh is vice president of sales for Philipsburg, Penn.-based SurferQuest, a company that specializes in public Internet kiosks. He says there are three kinds of hackers in the kiosk world: those who want to use the machine for free, those who mischievously want to crash the machine, and those whose motives are far darker.
"The third hacker is the dangerous one," he said. "He wants to see what every user does on the PC. He gathers the info and steals identities for various purposes."
This kind of data theft can be either relatively innocuous or potentially disastrous, depending chiefly on the application; the stakes are higher with information stolen from a public Internet kiosk than from a self-service grocery checkout.
"You have no idea what we found on computers for public use in the field," he said. "Credit card numbers, user names and passwords, bank accounts, personal chat logs, important company documents Â… we have seen it all."
Most kiosks run on Microsoft Windows - and hackers of all skill levels are intimately familiar with that platform, since they probably have a copy at home that they can experiment on.
"Windows is likely the most difficult operating system to hacker-proof, mainly because of its ubiquitous nature and its role as target for the hacker community," said Thomas Smith, president of Portsmouth, R.I.-based MontegoNet. "Kiosks make a unique target because of their open public nature."
A machine under attack
Hackers mischievous and benign work in a number of ways, across a spectrum of skill levels. On one end are elaborate cracks involving USB sticks and custom HTML code; on the other are tricks as simple as unplugging the box.
"Interruption of the power supply will initiate the restart of the PC," said Heinz Horstmann, chief executive officer of SiteKiosk, manufacturers of a self-titled software package that aims to make kiosks secure. "During the reboot process, the user has access to the BIOS if it is not password protected, or even worse, access to Windows Safe Mode by pressing F8."
|
Smith points out two widely known key combinations which can be used to devastating effect: CTRL+N (opens a new browser window) and CTRL+O (open a file). "These are good hacking holes as hackers know that once they get a location bar available, entering C:\ will open the machine to attack," he said.
Many of the most intimidating challenges in this field come when dealing with kiosks that implement Internet access in one form or another, either as a core retail service or as part of the back-end to another application. Two key issues arise when dealing with public Internet access: cached material and malicious code.
The problem of what to do with cached material is pretty simple, according to most experts: just clear it out on a regular basis, normally when the user logs off the machine. Mike Grubbs, general manager of Reston, Va.-based Connectivit-e Inc., said his company's Internet kiosks wipe the cache clean after each use, and also give users the opportunity to flush it themselves during the session.
But what about users that forget to log out? Some devices use a proximity sensor and end the session when the person walks away, while others use a simple inactivity timer.
Timers bring headaches of their own. Set the timeout value too high, and a passerby might see the logged-in session and begin using it. Set it too low, and it could log a user out while they're reading a long document, creating massive frustration.
Mothersbaugh points out that even if you manage to flush the cache comprehensively and at the appropriate time, that still might not be enough.
"A lot of leftover user content can be erased when the cache is flushed, but not everything," he said. "Keystroke logs can be hidden anywhere on the machine. Spyware and saved documents are still on the PC after flushing the cache, as are all chat logs."
Predatory code
When it comes to malicious code, viruses are the most widely understood threat, with spyware a close second.
Web sites themselves can become culprits, too. Hackers can place malicious code within the HTML of one of their own Web pages, then visit that page using the kiosk browser. This could be something as complex as a destructive ActiveX control, or as simple as a few lines of JavaScript code that open an alert window.
This kind of embedded threat represents a great conundrum for kiosk developers. Technologies such as Flash, JavaScript and ActiveX offer enhanced functionality and make the user's experience better; Flash, for example, has become so widely used that an Internet kiosk might be considered lacking if it were not enabled. But each of these technologies offers greater control of the computer to the Web page designer, and if that designer has harmful intent, that can be a very bad thing.
What can be done
Now that we've shaken you up, it is time for some solutions. Internet kiosks can be made secure, and the best way to do it is through a combination of hardware and software methods.
"We use the ultimate protection - a recovery card that protects the hard drive and CMOS settings from all forms of malware - worms, viruses, spyware," said Grubbs. "Whenever the kiosk is rebooted, it reverts back to its original starting point, wiping out any infections acquired during previous sessions. Since this is a hardware approach, no software can disrupt it."
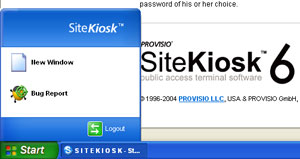 |
The replacement shell offered by SiteKiosk restricts user choices to allowed components. |
This approach basically gives you a brand new software installation at each start-up. From the kiosk's view, every reboot is like Groundhog Day.
The software side can be a bit more involved, chiefly due to the complexity and huge array of features offered by Windows. Of paramount importance is covering the default Windows interface, or shell, with a more restrictive GUI that only allows certain commands and actions.
"Replacing the standard Windows Explorer shell with a secure, watchdog-type shell prevents the majority of attacks, including any and all bad keystroke combinations," Smith said. Proprietary tools like this can also disable file downloads, prevent users from executing files, and filter Web sites based on URLs or other criteria.
Once things are tweaked to perfection and the units are in the field, the ongoing work begins: keeping up with evolving threats, performing regular software maintenance and upgrades, and staying informed.
"Hackers will continue to evolve their approaches and find new ways to invade Windows-based terminals," Grubbs said. "At the moment, however, the defense technologies have pretty much caught up to the hacker techniques."
So there, at the end of the day, you finally have some good news. It's a problem, but it is one that can be solved.
 ChatGPT
ChatGPT Grok
Grok Perplexity
Perplexity Claude
Claude











